Microsoft ends support for Internet Explorer on June 16, 2022.
We recommend using one of the browsers listed below.
- Microsoft Edge(Latest version)
- Mozilla Firefox(Latest version)
- Google Chrome(Latest version)
- Apple Safari(Latest version)
Please contact your browser provider for download and installation instructions.
July 18, 2018
NTT Discovers Novel Privacy Threat "Silhouette" in Social Web Services Prompting Collaboration with Twitter, Microsoft, and Mozilla to Improve Security Mechanisms of Major Global Services and Browsers
Nippon Telegraph and Telephone Corporation (NTT; Head Office: Chiyoda-ku, Tokyo; President & CEO: Jun Sawada) has discovered a novel privacy threat in social web services (SWSs)*1 and developed a technique for evaluating this threat. This threat arises when a user of a SWS visits a third-party website with malicious intent. It has the potential of identifying the name of that user's SWS account from that third-party site and exploiting that account name for various types of attacks involving the abuse of personal information, online fraud, etc. This "Silhouette" threat can be evaluated by a technique that we developed, and using this technique, we have already discovered SWSs that are vulnerable to this threat.
NTT is sharing information with service providers, browser vendors, and other parties that could be affected by this threat prior to the occurrence of any damage and is cooperating with them in implementing countermeasures in actual services and web browsers including Twitter, Microsoft Edge, Internet Explorer, and Mozilla Firefox using this evaluation technique. In this way, we are preventing SWS account names from being identified by third parties through this threat and making it safer for all users to use and enjoy SWSs.
Details of this privacy threat and evaluation technique were presented at 3rd IEEE European Symposium on Security and Privacy (Euro S&P 2018)*2, a distinguished academic conference in cyber security held by IEEE in April 2018 in the United Kingdom.
1.Background and History
In recent years, a wide variety of SWSs have come into existence on the Internet as typified by social networking services (SNSs) and video sharing sites. One survey reported that each user has at least five SWS accounts on average.
Privacy problems in SWSs include the leaking of registration details or private information in posts, but it is also known that simply using a SWS poses the risk of account-name identification from a third-party website accessed by the user. The privacy threat announced here relates to an account identification problem that we have recently discovered. At present, many SWSs have yet to implement any countermeasures against this threat.
2.Overview of the threat and our efforts
If a user of a SWS happens to visit a malicious third-party website, this threat has the potential of identifying the name of the user's SWS account from that third-party site. For example, search results, advertisements commonly included on websites, and links included in e-mail can provide access to a malicious site completely unrelated to that user's SWS. The malicious site can then secretly communicate with the SWS that the user is apparently using and identify the name of the user's SWS account.
Here, the condition for such account identification to take place is that a user who is currently logged into a SWS vulnerable to this threat visits a malicious third-party website while on a computer or mobile-device web browser. A typical SWS includes a mechanism for automatically maintaining a logged-in state until the browser's cookie*3 is deleted by some operation such as an explicit logout. As a consequence, a user who has used a SWS targeted by this threat even only once sometime in the past may become a target for account identification.
We have established a technique for evaluating whether a SWS is vulnerable to this new threat. We have also clarified that several well-known SWSs with a global presence are in a state in which account names can actually be identified. We have therefore shared threat details and countermeasures with SWS operators and performed joint experiments to test the effectiveness of these countermeasures. Through these activities, Twitter has been able to prevent the threat of account-name identification by changing its SWS specifications to improve its security mechanism. In addition, the SameSite attribute*4 used for cookies has been added to some major browsers such as Microsoft Edge, Internet Explorer, and Mozilla Firefox, to avoid threats that can be generated by the technique uncovered in our research or similar techniques. Such activities have contributed to significant improvement in the safety of many SWSs now being used throughout the world. They also mean that providers and operators including NTT will now be able to use rich functions to design secure web services going forward. From either a short-term or medium/long-term perspective, these research achievements have been instrumental in creating an environment in which the Internet is even safer to use for users anywhere in the world.
3.Features of technology
We here explain the working principle of this threat. This threat is established by exploiting a function called "user blocking" that is widely adopted in SWSs. The original purpose of this function was to provide a legitimate user a means of controlling whether another (possibly malicious) user may view one's own pages with the aim of protecting oneself from harassment, spam, or other undesirable activities. Of importance here is that a malicious user can also control the visibility of pages from legitimate users.
As a preliminary step, the malicious third party creates personal accounts within the target SWS (referred to below as "signaling accounts") and uses these accounts to systematically block some users on the same service thereby constructing a combination of non-blocked/blocked users (Fig. 1). This pattern can be used as information for uniquely identifying user accounts.
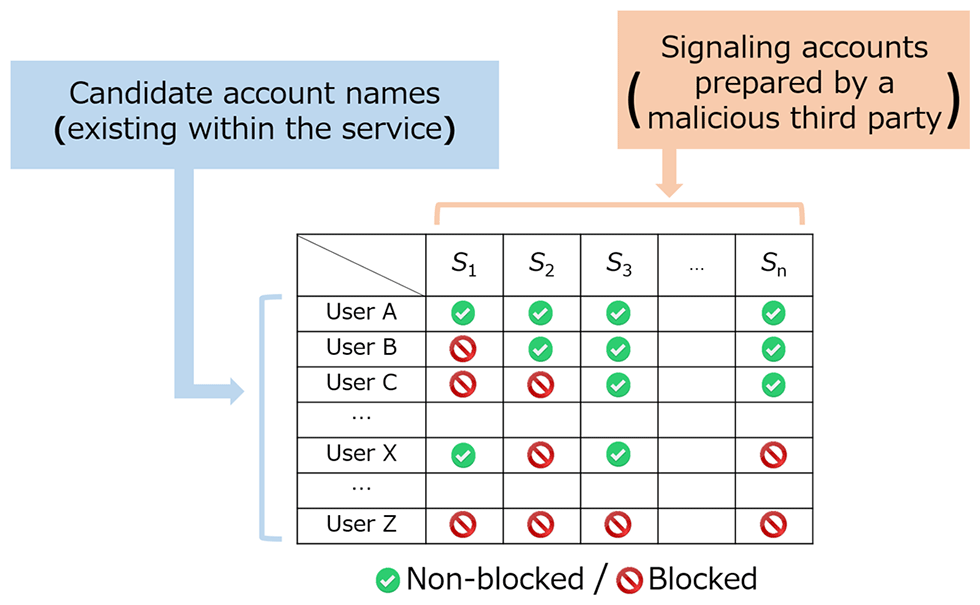 Fig. 1: Example of non-blocked/blocked settings for uniquely identifying user accounts
Fig. 1: Example of non-blocked/blocked settings for uniquely identifying user accounts
At the time of identification execution, that is, when a user visits a website on which a script for identifying account names has been installed, that user will be forced to communicate with pages of each of those signaling accounts. This communication, however, is protected by the Same-Origin Policy*5, so the third party will not be able to directly obtain the content of a response from such a communication.
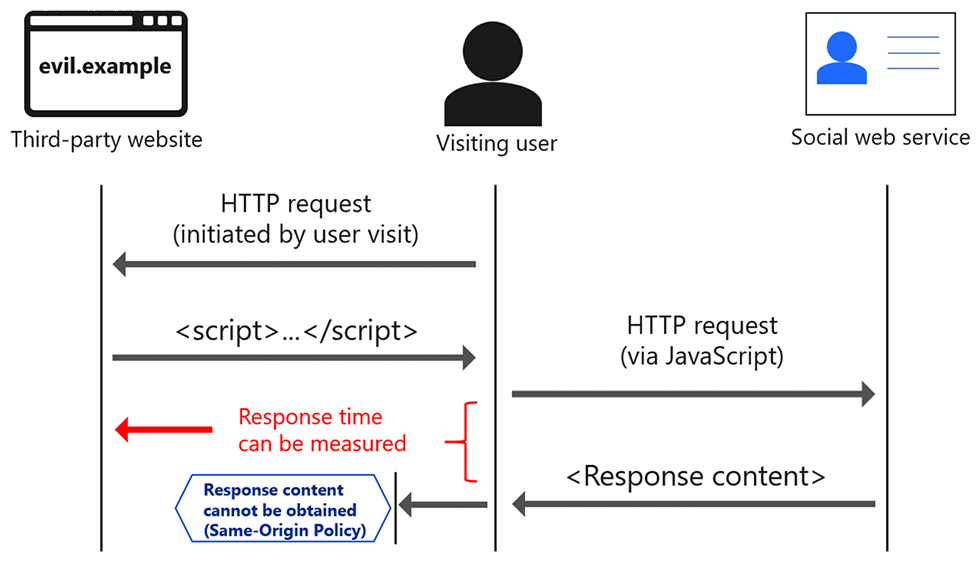 Fig. 2: Protection of response content by Same-Origin Policy
Fig. 2: Protection of response content by Same-Origin Policy
On the other hand, communication response time is statistically different depending on whether that content is visible or invisible. The malicious third party can use this difference to infer whether a visiting user is blocked or non-blocked from each of the signaling accounts, and finally, to compare the results of this inference with the previously constructed pattern. In this way, the malicious third party can identify account names in the SWS of those users.
An attack that makes use of real-space information such as response time as described above and attempts to steal sensitive personal information or break ciphers is generally called a "side-channel attack." In this regard, the approach taken by our risk evaluation technique is to first check whether a malicious user can enable/disable viewing by other users in the SWS targeted for evaluation and to then check whether that viewing enable/disable information can be obtained by a side-channel attack.
To counter this type of attack, the SWS can apply techniques such as checking Referer to assess the validity of an HTTP request or assigning the SameSite attribute to cookies. In addition, users of a SWS vulnerable to this threat can use the private browsing function when visiting a third-party site or make sure to log out when finished with the service thereby avoiding account-name identification. For details on these countermeasures, please see the page describing this threat (http://www.ntt.co.jp/sc/project_e/cybersecurity/silhouette.html).
4.Future Developments
As part of its R&D initiatives in cyber security, NTT will continue to develop techniques for evaluating new threats to web services as reflected by the risk evaluation technique reported here. At the same time, NTT is committed to collaborating with related institutions whenever a new problem is discovered to continuously raise the safety of the Internet. Going forward, NTT will strive to provide robust services while promoting secure web services and web browsers in society and the safe and secure use of the Internet.
Publication information
T. Watanabe, E. Shioji, M. Akiyama, K. Sasaoka, T. Yagi, and T. Mori, "User Blocking Considered Harmful? An Attacker-controllable Side Channel to Identify Social Accounts," Proceedings of the 3rd IEEE European Symposium on Security and Privacy (Euro S&P 2018), April 2018
Terminology
- SWS:
A web service consisting of content posted by users, messaging between users, etc. Typical examples include social networking services and video sharing sites as well as web forums, microblogs, online games, and auction sites. - Euro S&P:
A top-level international conference in the cyber security field held by IEEE for presenting cutting-edge technologies in this field. - Cookie:
A function enabling a web service to store information in the web browser of the visiting user to manage user settings, logins, sessions, etc. or the information so saved. - SameSite attribute:
An option that temporarily discards login status under specific conditions and preserves a state preventing the leaking of user information by giving the web-service side flexible control over the sending of cookies to the server side. Prior to the research achievements reported here, this option was available only in the Google Chrome browser or Chromium-based browsers such as Opera. - Same-Origin Policy:
A restriction included in a browser for protecting information from undesirable meddling or use in the event of communications from some origin (host name, port number, scheme) to another origin.
Contact information
Public Relations
NTT Service Innovation Laboratory Group
E-mail: randd-ml@hco.ntt.co.jp
Information is current as of the date of issue of the individual press release.
Please be advised that information may be outdated after that point.
NTT STORY
WEB media that thinks about the future with NTT











