Microsoft ends support for Internet Explorer on June 16, 2022.
We recommend using one of the browsers listed below.
- Microsoft Edge(Latest version)
- Mozilla Firefox(Latest version)
- Google Chrome(Latest version)
- Apple Safari(Latest version)
Please contact your browser provider for download and installation instructions.
September 26, 2024
NTT Corporation
World's First: Elimination of Practically Inconvenient Conditional Restrictions in Registered Attribute-Based Encryption
Improving the practicality of innovative encryption with both security and functionality
News Highlights:
- Construct complex registered attribute-based encryption assembled from easy-to-analyze component techniques
- Eliminate the security concern of "master secret key" leak
- There are no restrictions on access control policies, such as allowing NOT, allowing the same attribute to be used multiple times in policies, and not having to specify which attribute to use at system setup
TOKYO - September 26, 2024 - NTT Corporation (Headquarters: Chiyoda Ward, Tokyo; Representative Member of the Board and President: Akira Shimada; hereinafter "NTT") has developed an encryption method that enables practical access control in registered attribute-based encryption, which was not possible with conventional methods. Registered attribute-based encryption is a new type of attribute-based encryption that addresses the security concerns of attribute-based encryption, a public key encryption technology with access control. In this study, we constructed the world's first attribute-based encryption that achieves both security and practical access control. This achievement was presented at the 44th Annual International Cryptology Conference (Crypto 2024)1, a prestige international conference on cryptology.
1. Background
Attribute-based encryption is a public key encryption method that realizes decryption only with a key that matches the policies by incorporating conditional decryption such as ('Human Resource Department AND Manager' OR Accounting Department) into the ciphertext used to encrypt data and adding attribute information such as "General Manager of Accounting Department" to the secret key used to decrypt the ciphertext (Figure 1). In attribute-based encryption, public information called the master public key is used in addition to the data to be encryption data and the policy. While attribute-based encryption is expected to be applied to in-house data access control and content distribution services, each user's secret key is generated by a key generation center, which has strong authority to decrypt all ciphertexts. If the secret information held by this key generation center, called the master secret key, is leaked, all data in the system will be decrypted (Figure 2). In other words, the key generation center has remained a single point of failure in security concerns.
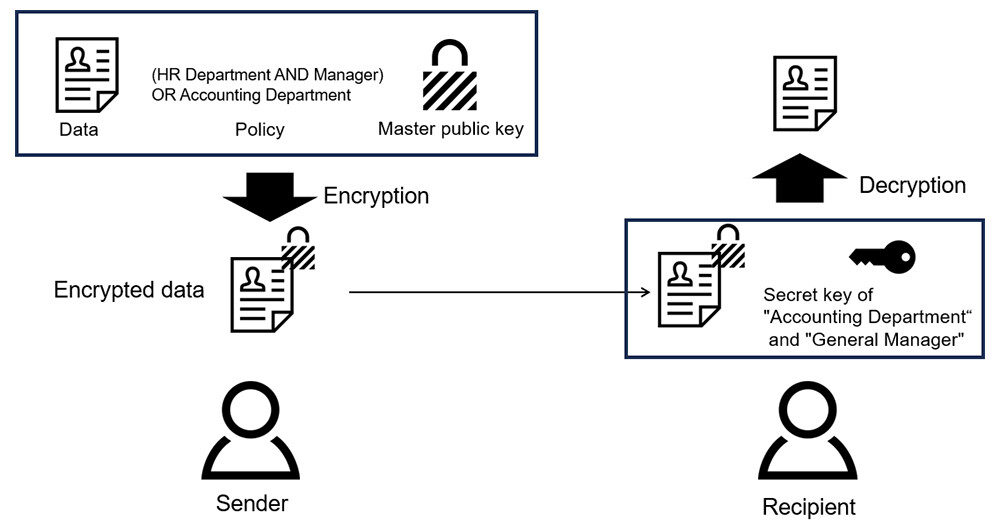 Figure 1 Example of Using Attribute-Based Encryption
Figure 1 Example of Using Attribute-Based Encryption
In recent years, attribute-based encryption without a key generator called registered attribute-based encryption, has been proposed to solve this problem. In registered attribute-based encryption, each user generates their own public key and secret key and registers the public key and their attribute information in the registration server (Figure 3). The role of the registration server is to compress the public key registered by each user and to generate the master public key required for encryption. Since it does not have any secret information, an attack does not affect the security of the system. The ciphertext is decrypted only if the policy is satisfied by each user's secret key. However, previous registered attribute-based encryptions have some inconvenient limitations in practical use, such as not being able to use policies containing NOT and not being able to use the same attribute multiple times in a policy.
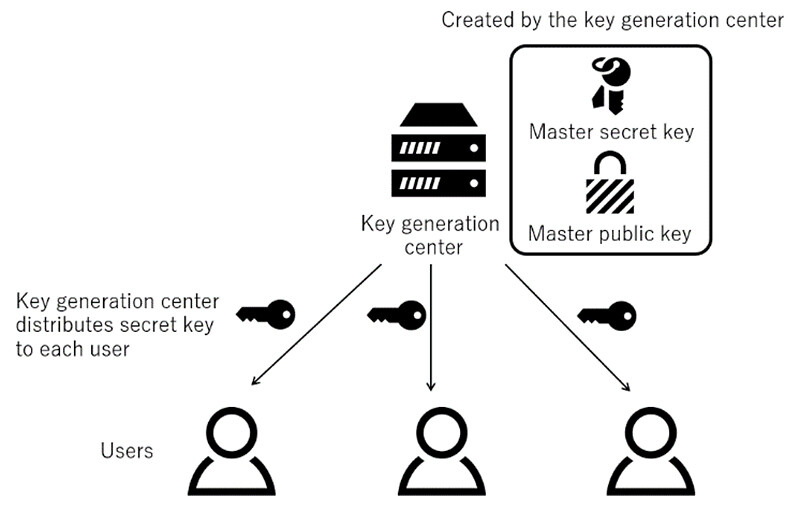 Figure 2 Key Generation Model for Attribute-Based Encryption
Figure 2 Key Generation Model for Attribute-Based Encryption
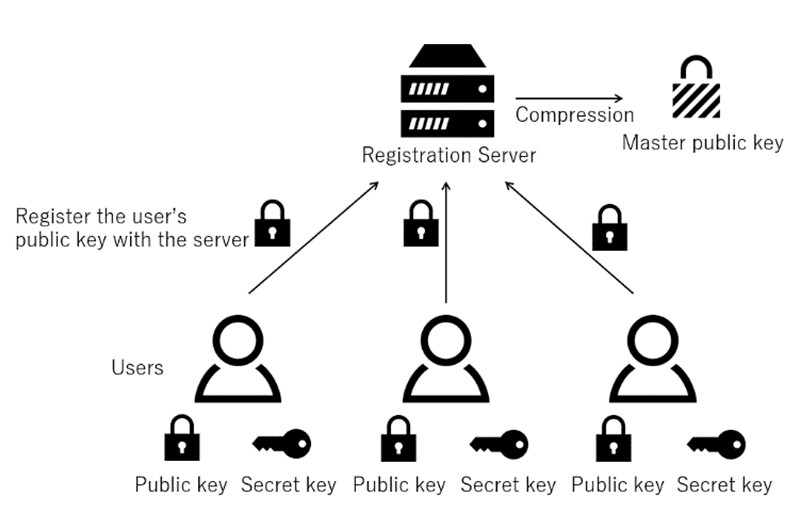 Figure 3 Key Generation Model for Registered Attribute-Based Encryption
Figure 3 Key Generation Model for Registered Attribute-Based Encryption
2. Research results and technical points
In a paper2 co-authored by NTT and the National Institute of Advanced Industrial Science and Technology, NTT devised a series of conversion techniques to convert registered attribute-based encryption, which has many restrictions on policy decryption, to registered attribute-based encryption, which has no restrictions. By repeatedly applying these transformations to the existing registered attribute-based encryption, we showed that it can be converted to one that can handle policies such as including NOT, with unbounded size, and with an unbounded number of use of the same attribute. An approach to directly devising registered attribute-based encryption without such restrictions was considered, but it was difficult to prove and implement the security of complex encryption methods. Therefore, we have shown for the first time in the world that a registered attribute-based encryption can be constructed by focusing on a technique to assemble a complex registered attribute-based encryption from simple attribute-based encryption and an elemental technology that is easier to analyze than a series of transformations (Figure 4).
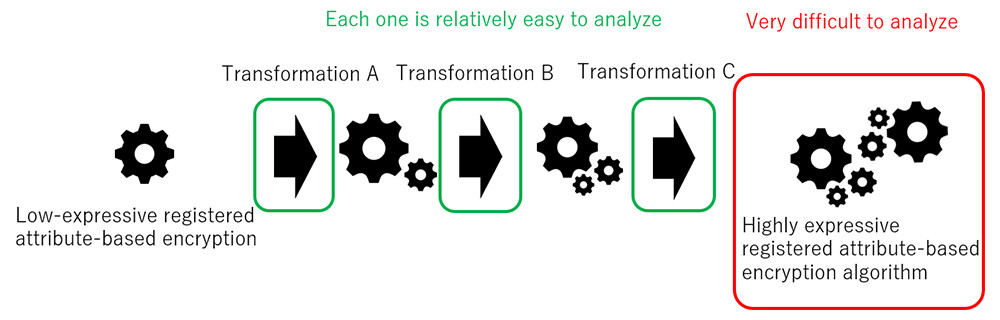 Figure 4 Transformation Image of Registered Attribute-Based Encryption
Figure 4 Transformation Image of Registered Attribute-Based Encryption
The advantages of this technology over existing technologies are shown in Table 1. (1) The data encryption time does not depend on the number of decryptors, (2) there is no master secret key in the system, and (3) there are no restrictions on the policies.
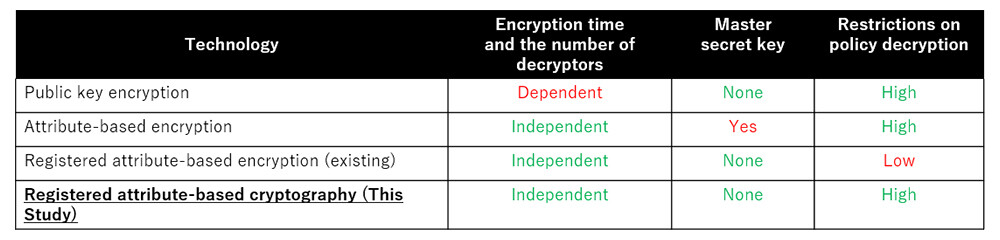 Table 1 Comparison with Conventional Technology
Table 1 Comparison with Conventional Technology
3. Outlook
By constructing a registered attribute-based encryption that can handle practical conditional decryption, this technology is expected to improve the security of data systems involving a large number of users, such as content data in content distribution services like video and music, and organizational data held by companies, and to significantly reduce the risk of data leakage due to unauthorized access.
We will continue to research and develop more practical registered attribute-based encryptions to solve the problem of inefficiency of the final registered attribute-based encryption resulting from repeated transformations.
[Glossary]
1.CRYPTO2024 https://crypto.iacr.org/2024/
2.A Modular Approach to Registered ABE for Unbounded Predicates. Nuttapong Attrapadung (AIST), Junichi Tomida (NTT Social Informatics Laboratories)
About NTT
NTT contributes to a sustainable society through the power of innovation. We are a leading global technology company providing services to consumers and businesses as a mobile operator, infrastructure, networks, applications, and consulting provider. Our offerings include digital business consulting, managed application services, workplace and cloud solutions, data center and edge computing, all supported by our deep global industry expertise. We are over $97B in revenue and 330,000 employees, with $3.6B in annual R&D investments. Our operations span across 80+ countries and regions, allowing us to serve clients in over 190 of them. We serve over 75% of Fortune Global 100 companies, thousands of other enterprise and government clients and millions of consumers.
Media contact
NTT Service Innovation Laboratory Group
Public Relations
nttrd-pr@ml.ntt.com
Information is current as of the date of issue of the individual press release.
Please be advised that information may be outdated after that point.
NTT STORY
WEB media that thinks about the future with NTT