Microsoft ends support for Internet Explorer on June 16, 2022.
We recommend using one of the browsers listed below.
- Microsoft Edge(Latest version)
- Mozilla Firefox(Latest version)
- Google Chrome(Latest version)
- Apple Safari(Latest version)
Please contact your browser provider for download and installation instructions.
May 12, 2025
NTT Corporation
World's First: Secure and High-Speed Advanced Digital Signature Technology for the Quantum Era
Distributed signature generation across 5 continents in 2.5 seconds—towards secure infrastructure for government and financial systems
News Highlights:
- We have developed the world's first fast and secure distributed digital signature system resistant to quantum computer threats.
- We have successfully demonstrated signature generation in an average of 2.5 seconds between servers across 5 continents, confirming solid performance on global real-world networks.
- We expect this technology to be deployed for secure, multi-user authentication and permission applications in systems such as electronic voting, government services, and finance.
TOKYO - May 12, 2025 - Through joint work with ETH Zurich in Switzerland, UC Berkeley in the United States, Aalto University in Finland, Bocconi University in Italy, and JPMorgan in the United States, NTT Corporation (Headquarters: Chiyoda, Tokyo; President and CEO: Akira Shimada; hereinafter "NTT") has developed "Ringtail"—the world's first two-round, post-quantum threshold signature scheme based on standard security assumptions. A threshold signature is an advanced cryptographic functionality that securely distributes a single signing key among multiple stakeholders, allowing a valid digital signature to be generated only when a predetermined number of participants (above the threshold) collaborate (Figure 1). This greatly reduces the risks associated with single points of failure, such as misconduct by a single administrator, or key loss or theft, and is therefore applicable to areas like crypto-asset management, critical infrastructure and enterprise system administration, decentralized finance (DeFi), Web 3.0, and electronic voting systems.
Ringtail is the first scheme to combine the high efficiency (fewer communication rounds and faster performance), strong reliability (provable security), and future-proofness (resistance to quantum computers) required for such applications. We expect it to become a foundational technology for secure and trustworthy next-generation decentralized systems.
This paper will be presented at IEEE S&P 2025, to be held in San Francisco, USA, from May 12-15, 2025.1
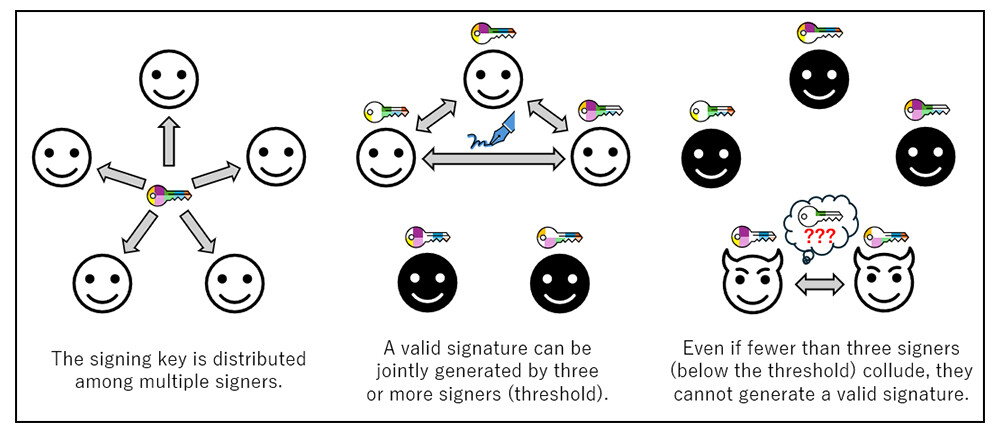 Figure 1 Image of Threshold Signatures
Figure 1 Image of Threshold Signatures
Note. White icons represent users participating in the protocol; black icons represent non-participating users.
Background
In plain digital signatures, the signing key is held by a single user who generates signatures by themself. However, in corporate environments and societal systems, concentrating critical authority in the hands of one person is often undesirable. For instance, internal control rules may require signatures from "three or more managers" to approve a purchase order; in cryptocurrency wallets, one needs to avoid the risk of asset loss due to a single key being lost or stolen.
Threshold signatures address these needs by offering a cryptographic mechanism that distributes signing authority among multiple parties and allows a valid signature to be generated only when a designated minimum number of participants cooperate.
This technology is increasingly being adopted in blockchain systems, Web 3.0, decentralized finance (DeFi), and decentralized autonomous organizations (DAOs)—all of which avoid centralized control or aim to distribute authority. In such systems, three key elements are of particular importance:
- Efficiency: Low communication overhead and minimal latency are essential to enable rapid consensus among globally distributed participants.
- Reliability: Since these systems often handle large assets or critical organizational decisions, they require a high level of security, supported by mathematical proofs.
- Future-proofness: Once the technology at the foundation of these systems is deployed, it is difficult and expensive to replace. Long-term security—especially against future threats like quantum computers—must therefore be ensured from the get-go.
Recently, in relation to point (3), it has become a major concern that most existing threshold signature schemes are based on RSA or elliptic curve cryptography, which are vulnerable to future general-purpose quantum computers. As a result, the development of post-quantum threshold signature schemes has become an urgent challenge.
Challenges in Existing Approaches
Several post-quantum threshold signature schemes have been proposed to date, primarily based on lattice-based cryptography. However, existing schemes have faced challenges in terms of efficiency or security.
In theory, arbitrary signature scheme can be converted into a threshold signature scheme using a technique called secure multi-party computation. However, most existing post-quantum signature schemes are poorly suited to this approach. The transformation process significantly increases computational cost, making it impractical in real-world applications. In lattice-based signatures, one major source of this overhead is an operation known as rejection sampling, which is often required to ensure security.
Recently, a lattice-based signature scheme called Raccoon, which avoids rejection sampling, was introduced. Based on this, a threshold signature scheme known as Threshold Raccoon2 was proposed. While Threshold Raccoon achieves low signature size and computational cost, it still requires three rounds of communication to generate a signature. This makes it less suitable for distributed systems where faster communication is essential.
To address this issue, Espitau et al. developed a two-round lattice-based threshold signature scheme3 as an improvement over Threshold Raccoon. However, the security of this scheme relies on a newly introduced and ad hoc assumption called AOM-LWE, which was specifically created for this scheme. Unlike well-established and extensively studied assumptions such as LWE, the solidity of this new assumption remains uncertain. As a result, there are concerns about adopting the scheme in highly sensitive applications such as financial systems, where a very high level of security assurance is required.
Key Features and Benefits of Our Technology
Our scheme Ringtail, the first two-round, post-quantum threshold signature scheme based on standard security assumptions, overcomes the aforementioned challenges.
Technical Highlights:
This works buildis upon the security proof techniques used in NTT's previous research on the lattice-based distributed signature scheme MuSig-L4,5, extends them and applies them to the two-round protocol framework proposed by Espitau et al. By relying on Gaussian distributions6 for the randomness generated within the protocol, the team successfully proved the scheme's security under the Learning With Errors (LWE) assumption—the most standard and widely trusted assumption in lattice-based cryptography.
Performance:
Compared to existing schemes such as Threshold Raccoon and the construction of Espitau et al., Ringtail achieves lower communication overhead in both key generation and signature generation, offering excellent efficiency.
Proof-of-Concept Experiment:
To evaluate real-world performance, servers were deployed across eight data centers located in Japan, Singapore, Germany, Ireland, Brazil, the East and West coasts of the United States, and Australia. These centers span five continents—Asia, Europe, North America, South America, and Oceania—introducing significant network latency between nodes. Testing the implementation under such geographically dispersed and realistically harsh conditions made it possible to validate the practicality of this scheme for global distributed deployments.
Experimental Results:
The experiment confirmed that even in the most latency-intensive scenarios—such as between Japan and Brazil—the entire distributed signing process completed in an average of approximately 2.5 seconds. (This includes both the offline preparation phase and the online signature generation and verification phase.) The average time required for the online signing operation itself was about 0.6 seconds, which is comparable to the physical latency between Japan and South America. This demonstrates the high efficiency of the protocol.
In operations requiring strong security and multi-party approval—such as multi-department authorization for high-value transfers in corporate financial systems, withdrawal of customer assets from cold storage at cryptocurrency exchanges, or collaborative decisions on critical system parameters in decentralized networks—this level of speed can be considered fully practical.
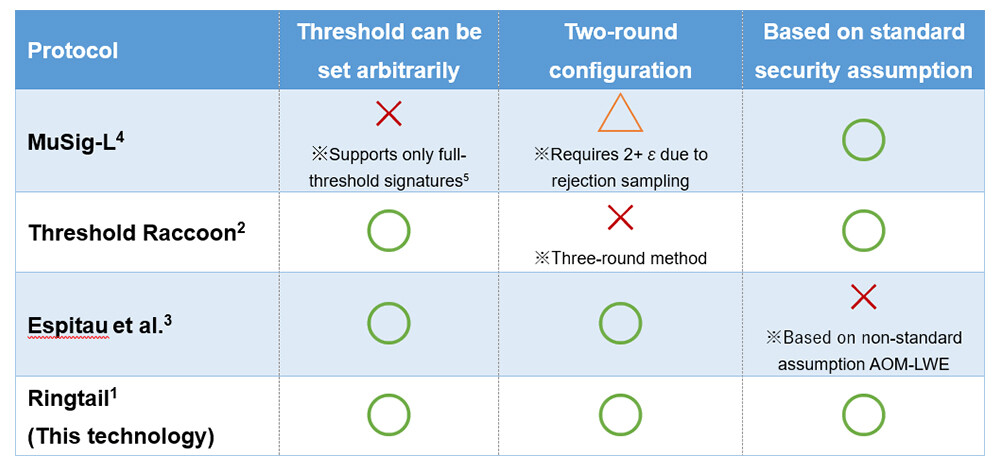 Table 1 Comparison of Methods by MuSig-L, Threshold Raccoon, Espitau et al. and Characteristics of Ringtail
Table 1 Comparison of Methods by MuSig-L, Threshold Raccoon, Espitau et al. and Characteristics of Ringtail
Outlook
Going forward, we will expand this technological approach to more advanced cryptographic functions, such as threshold group signatures that enable more complex access control. Through this, we aim to contribute to the realization of reliable decentralized systems, secure even in the era of quantum computing.
At NTT, we will continue to pursue research and development of cryptographic technologies that achieve both high security and excellent performance, ensuring they can be safely used in society.
1"Ringtail: Practical Two-Round Threshold Signatures from Learning with Errors." Cecilia Boschini, Darya Kaviani, Russell W. F. Lai, Giulio Malavolta, Akira Takahashi, Mehdi Tibouchi. In IEEE S&P 2025.
2"Threshold Raccoon: Practical Threshold Signatures from Standard Lattice Assumption." Rafael Del Pino, Shuichi Katsumata, Mary Maller, Fabrice Mouhartem, Thomas Prest, Markku-Juhani O. Saarinen. In EUROCRYPT 2024.
3"Two-Round Threshold Signature from Algebraic One-More Learning with Errors." Thomas Espitau, Shuichi Katsumata, Kaoru Takemure. In CRYPTO 2024.
4"MuSig-L: Lattice-Based Multi-signature with Single-Round Online Phase." Cecilia Boschini, Akira Takahashi, Mehdi Tibouchi. In CRYPTO 2022.
5While MuSig-L is structured in almost two rounds under standard security assumptions, it is not a general threshold signature scheme. Instead, it requires the consent of all users—what is called a "full threshold signature"—which limits its practical applications compared to typical threshold signature schemes.
6A Gaussian distribution is one of the most fundamental patterns used to describe how values vary. It forms a bell-shaped curve where most values cluster around the average, and fewer values appear as you move away from the average. In cryptographic technologies, the mathematical properties of this distribution often play a key role in proving the security of a scheme.
About NTT
NTT contributes to a sustainable society through the power of innovation. We are a leading global technology company providing services to consumers and businesses as a mobile operator, infrastructure, networks, applications, and consulting provider. Our offerings include digital business consulting, managed application services, workplace and cloud solutions, data center and edge computing, all supported by our deep global industry expertise. We are over $92B in revenue and 330,000 employees, with $3.6B in annual R&D investments. Our operations span across 80+ countries and regions, allowing us to serve clients in over 190 of them. We serve over 75% of Fortune Global 100 companies, thousands of other enterprise and government clients and millions of consumers.
Media contact
NTT Service Innovation Laboratory Group
Public Relations
Inquiry form
Information is current as of the date of issue of the individual press release.
Please be advised that information may be outdated after that point.
NTT STORY
WEB media that thinks about the future with NTT










